Kubescape
Kubescape is a K8s open-source tool providing a multi-cloud K8s single pane of glass, including risk analysis, security compliance, RBAC visualizer and image vulnerabilities scanning. Kubescape scans K8s clusters, YAML files, and HELM charts, detecting misconfigurations according to multiple frameworks
Some terminologies which are good to be understood:
Kubernetes is an open-source technology whose aim is to deploy, manage, orchestrate microservices which are found usually in containerized applications.
A container is a software package that contains all the dependencies needed to run a software.
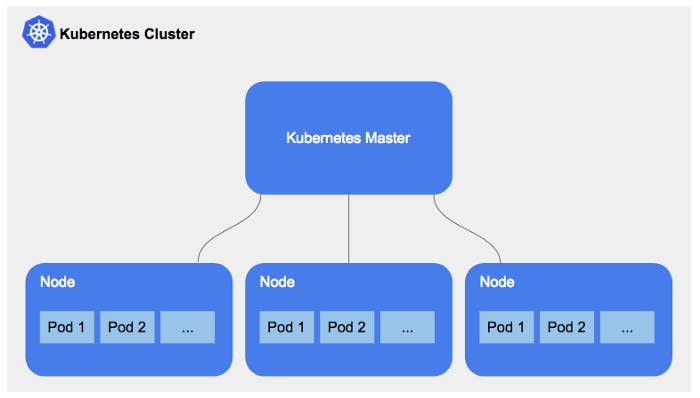
Kubernetes cluster is a set of nodes that run containerized applications. Nodes are machines categorized into one master and the rest are workers that are used to run these microservices.
YAML stands for Yaml Ain't a Markup Language. YAML is a data serialization language that is often used for writing kubernetes configuration files.
Helm is a package manager for kubernetes. It is the K8s equivalent of yum or apt, and deploys charts, which you can think of as a packaged application
Helm chart is a collection of all your versioned, pre-configured application resources which can be deployed as one unit.
Scan your cluster using kubescape
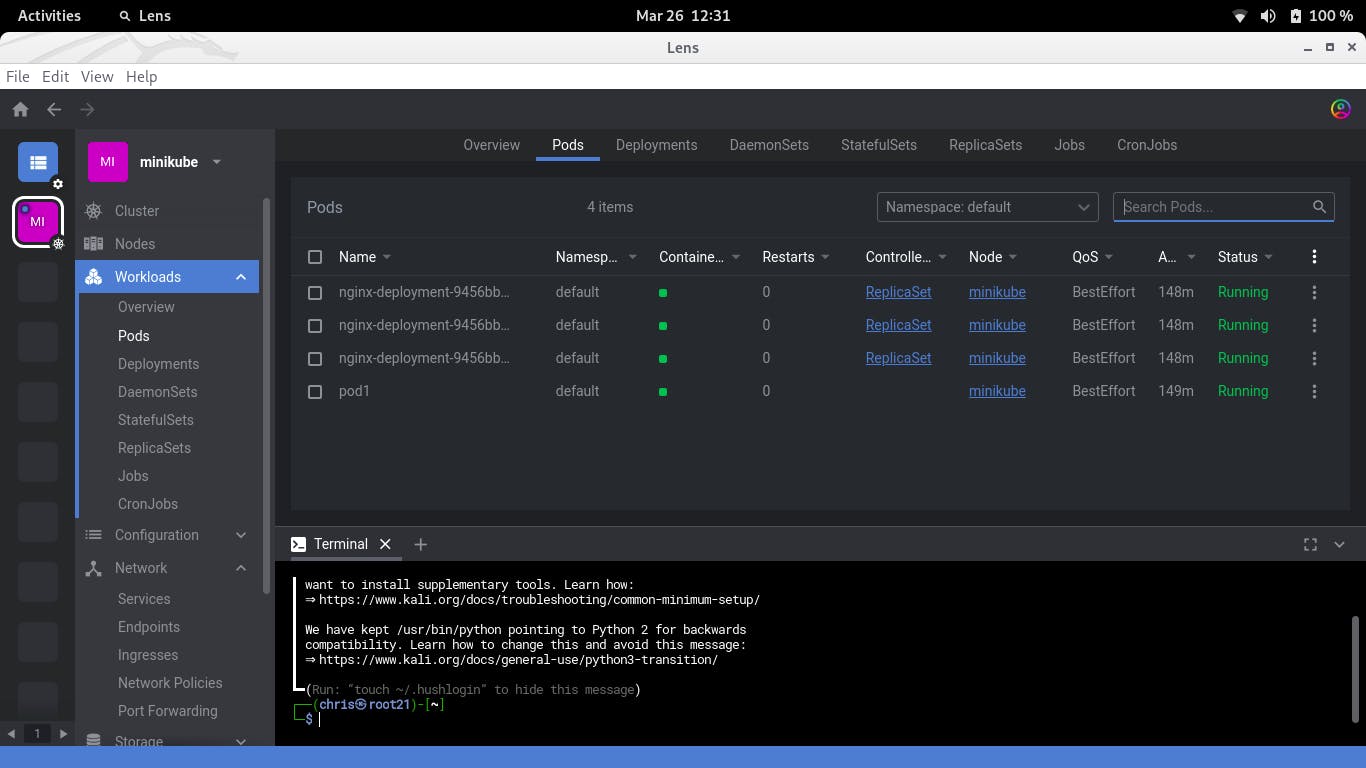
The first step is to start your cluster and for this purpose I was using minikube which is a local single-node kubernetes cluster
After starting your cluster, you need to start and deploy some resources which you will scan. I deployed a pod and a deployment with three replicas
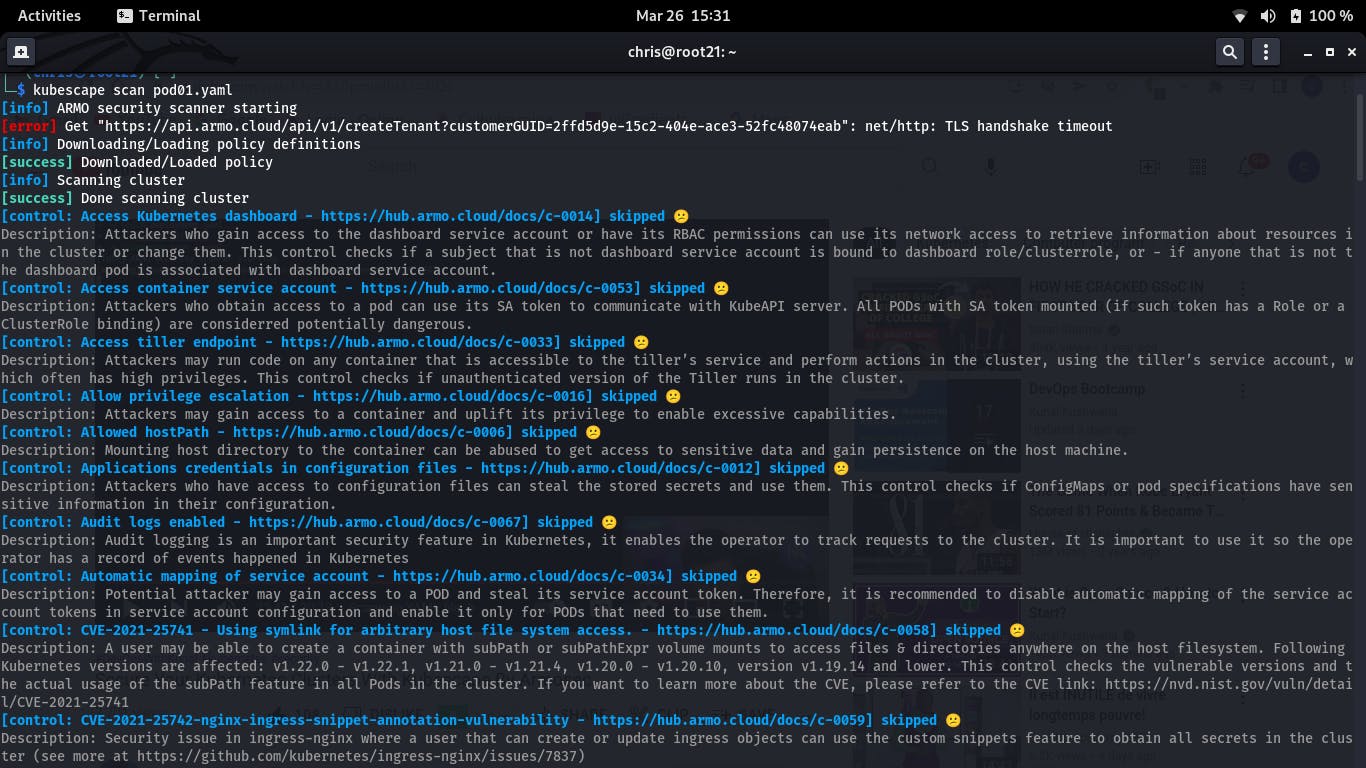
- Lastly, inorder to carryout my scan, I wrote down the command :
kubescape scan --submit --enable-host-scan
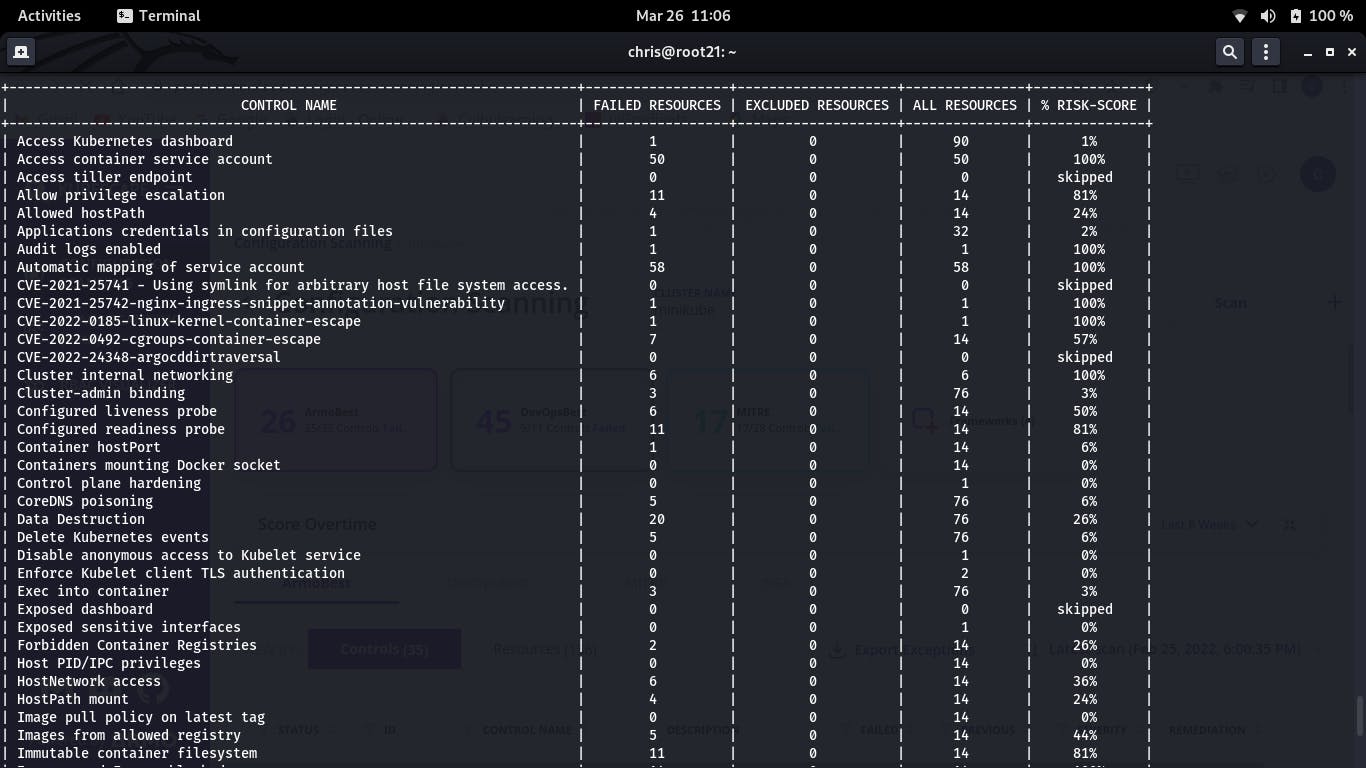
from website:
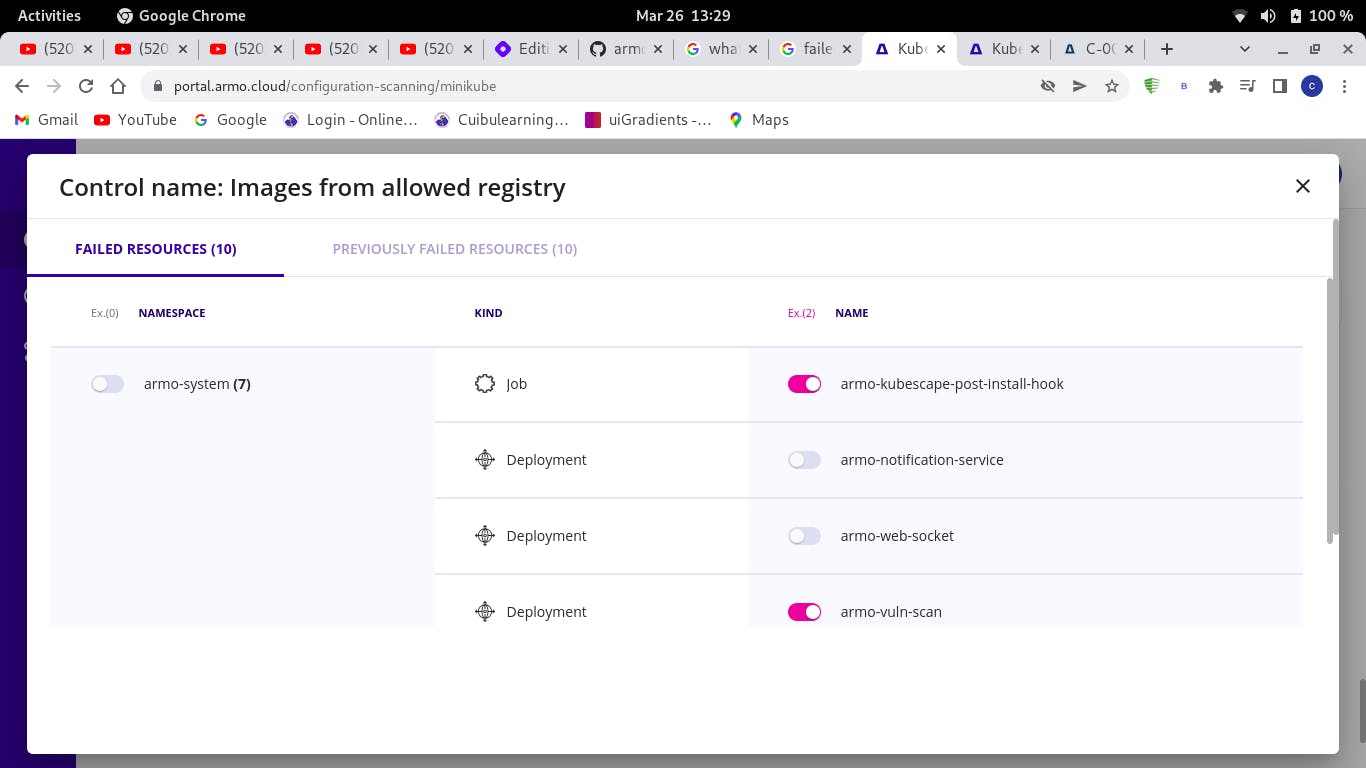
Create an exception
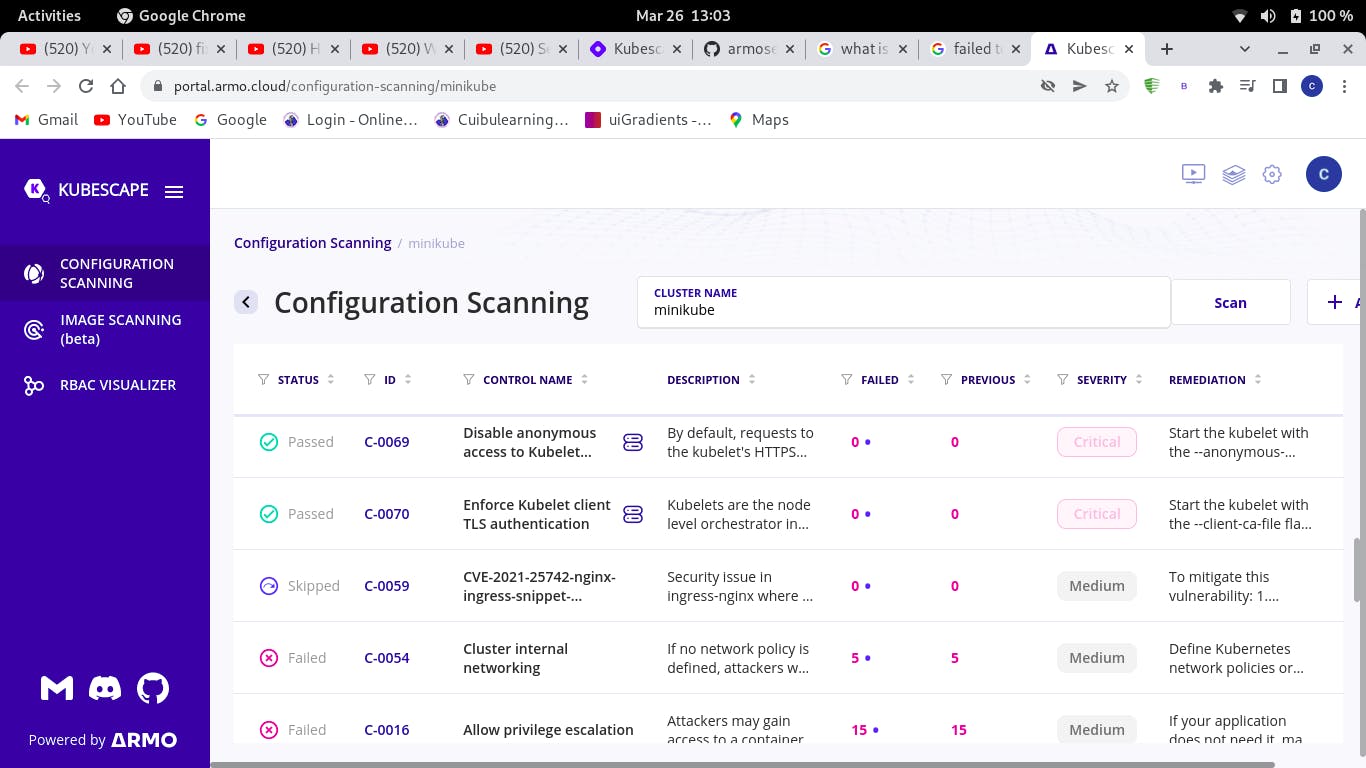
From the kubescape graphical user interface (website), target a control name
Click on the control name to open up the configuration environment for creating your exception
- According to your needs, enable the conditions required for your execption rule to be successful
Find and fix vulnerabilities in cluster using kubescape
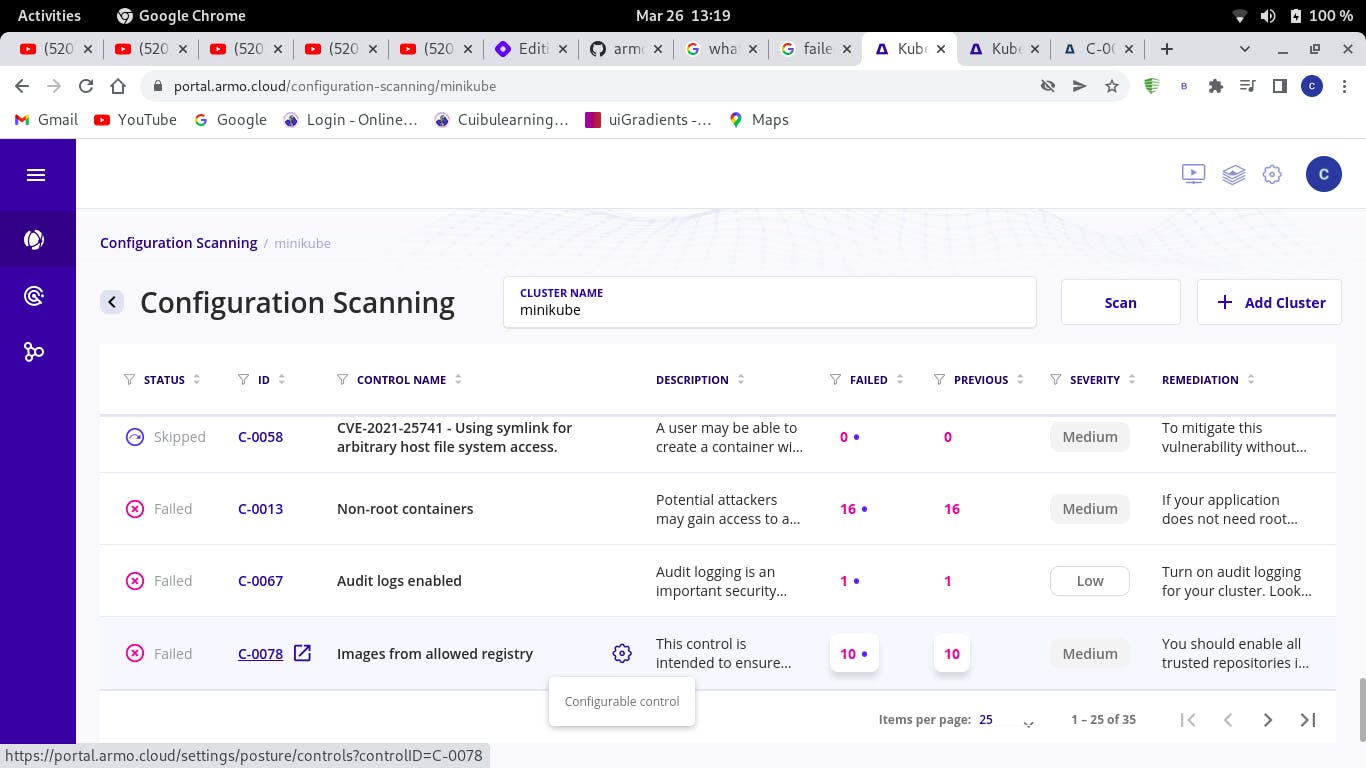
Select a control name, enter into the configuration settings
Select a resource having an issue which you intend to fix and click on the icon on the right side of that resource name
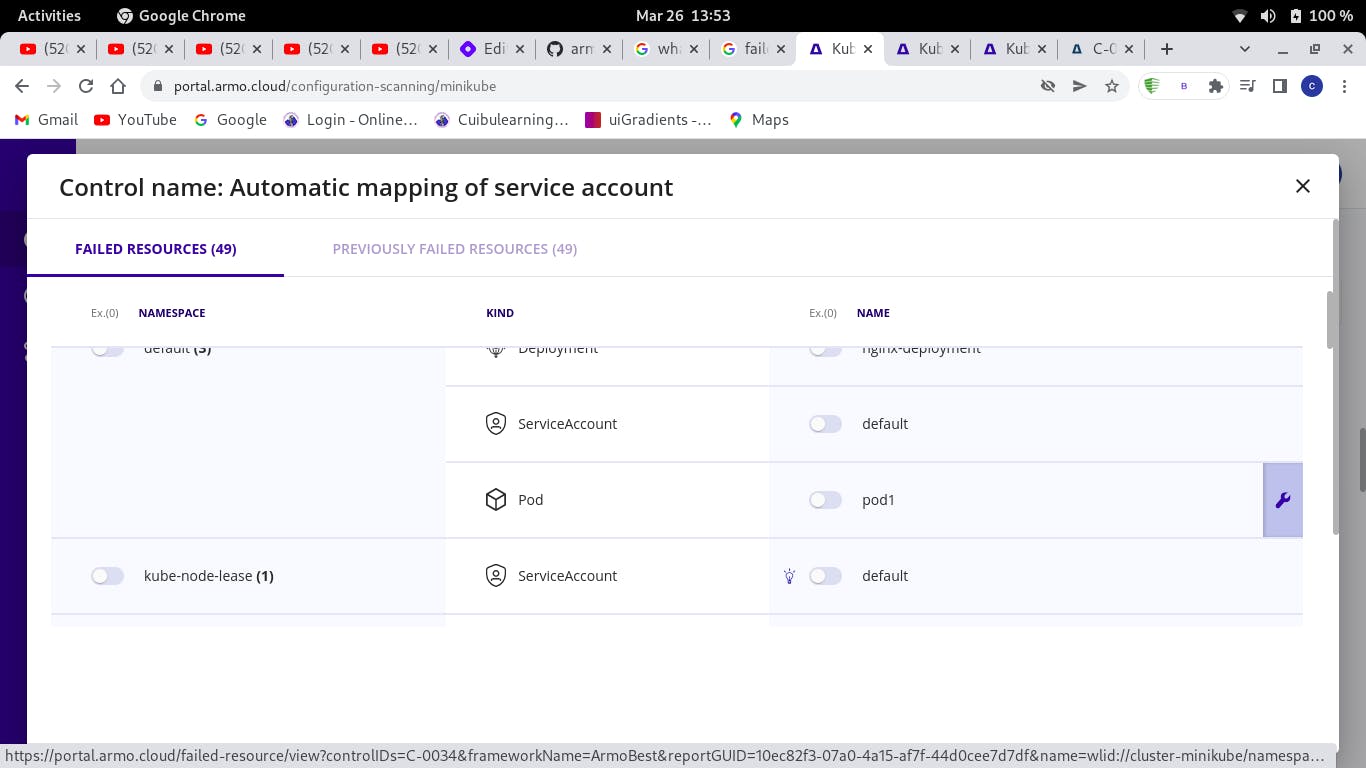
- You will be taken to a page showing you the configuration file (YAML) for that resource and will be pointed out where the problem is found
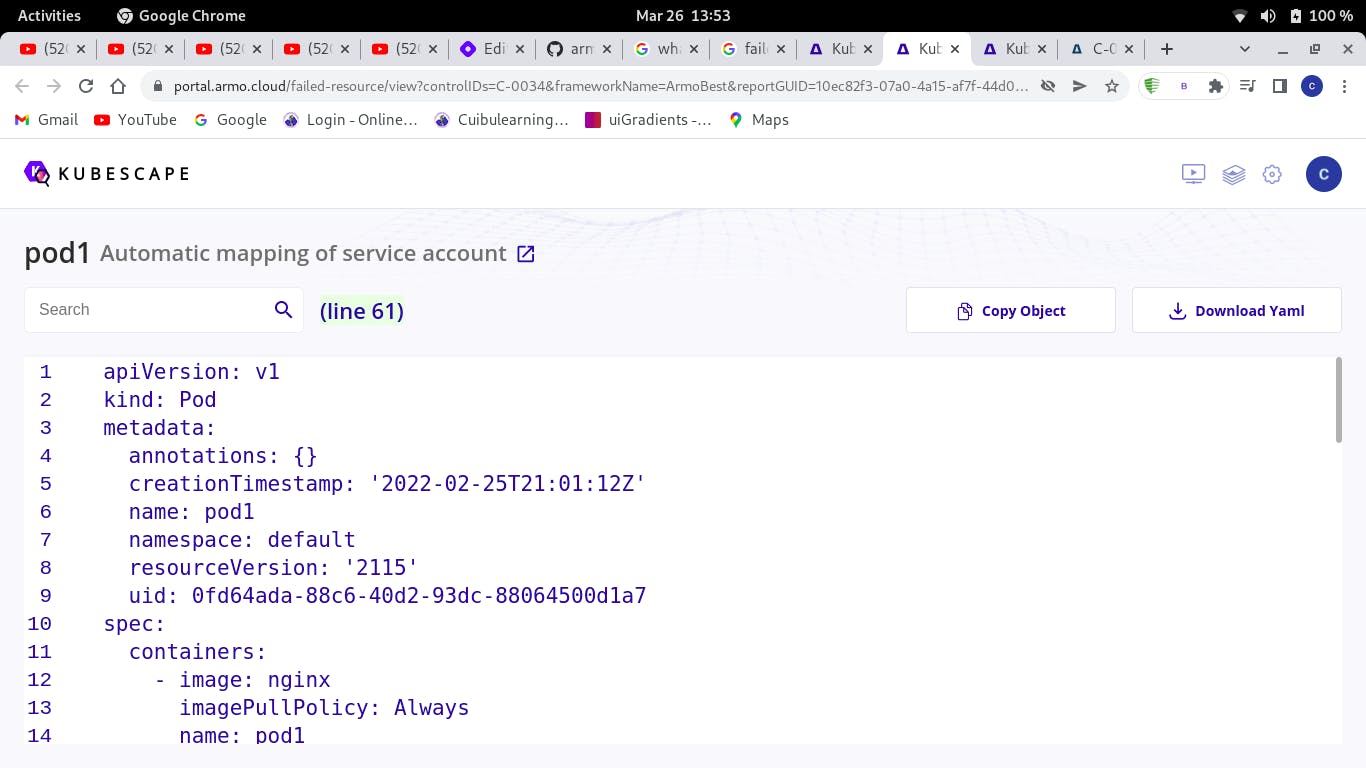
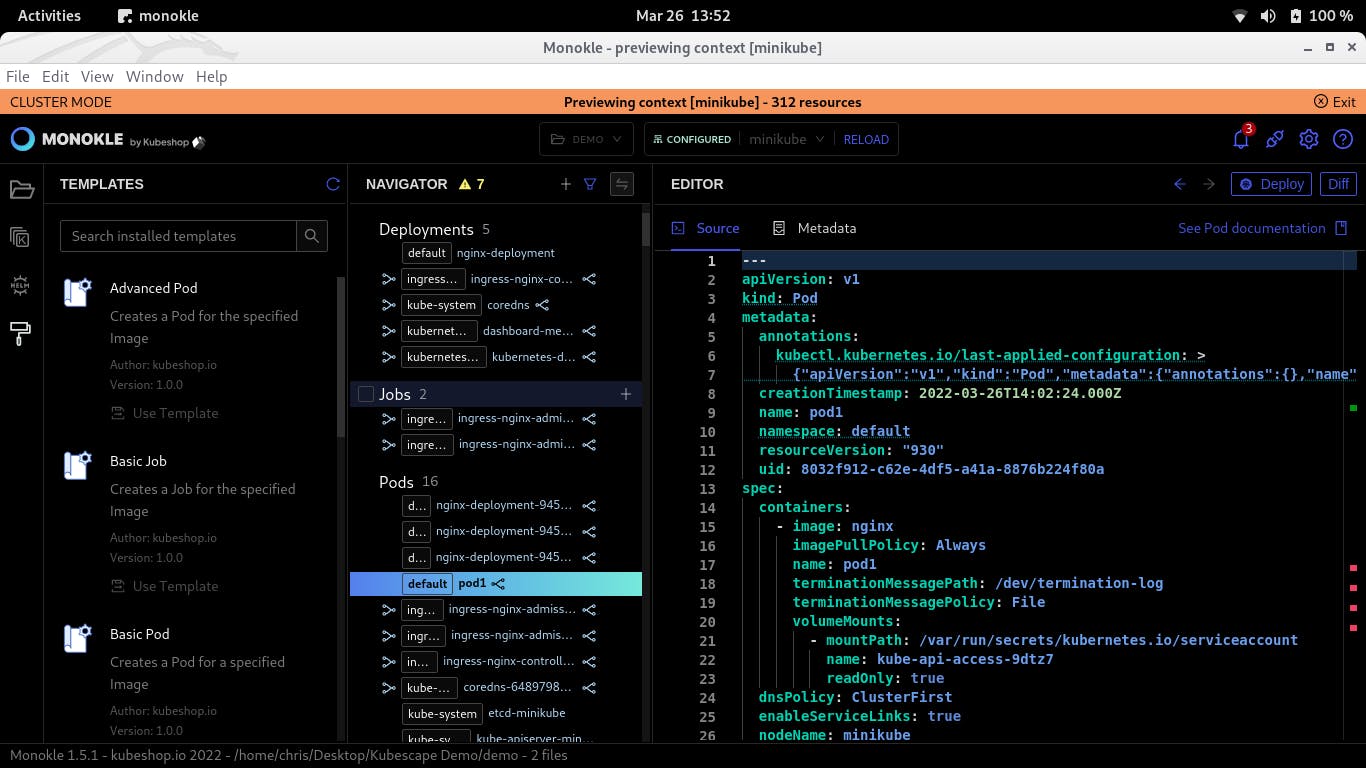
- After identifying the error, by the use of monokle you can go to where the file is for that resource is found and fix the issue
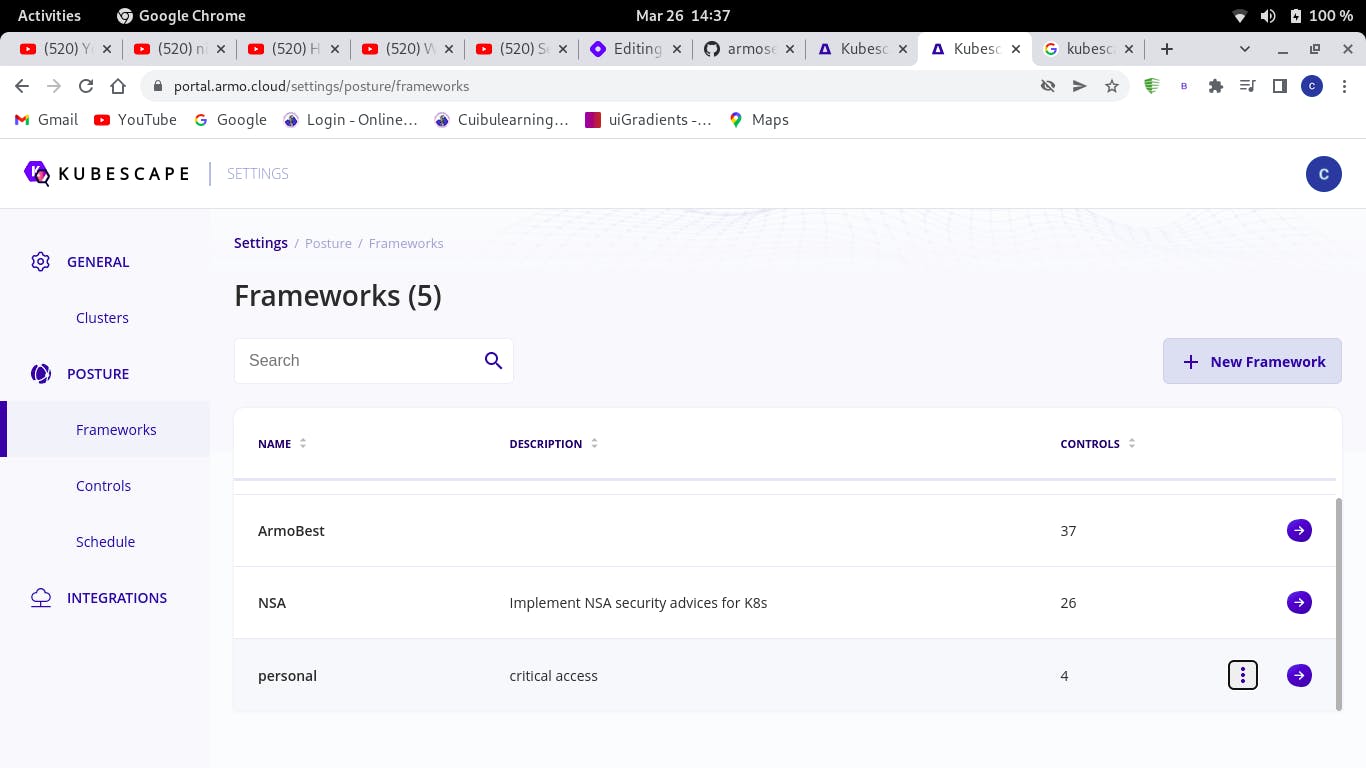
Create a custom framework
Go to the settings option on your kubescape interface
Select create framework, give it a name and a description
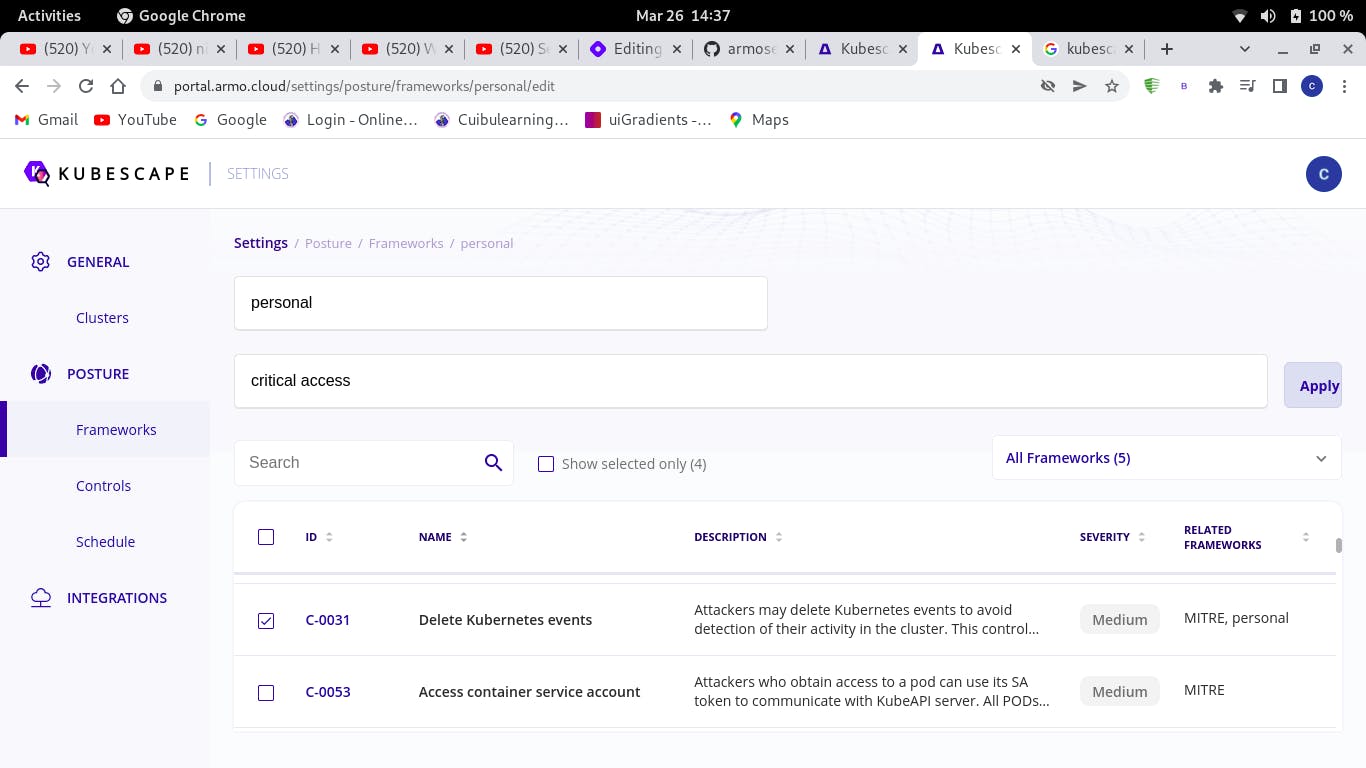
The controls included in my framework called personal are:
Cluster-admin binding which subjects have cluster admin permissions
SSH server running inside container which checks if pods have open SSH port
Exposed sensitive interfaces check if known components ar deployed and exposed services externally
Delete kubernetes events which identifies all subjects that can delete kunernetes events
Scan a YAML file
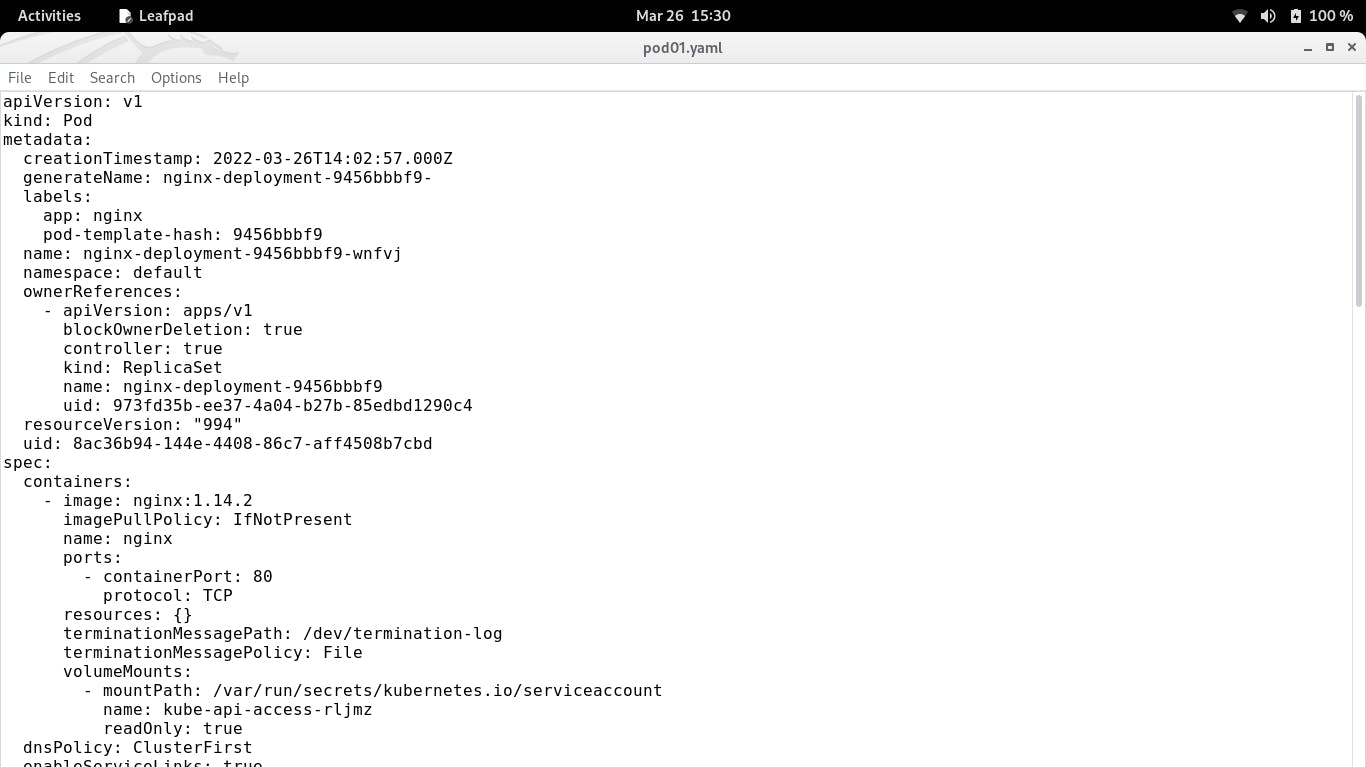
- Create the file and insert the code in it as shown below
- Type the command
kubescape scan pod01.yamland view the output: